SIN-07 Security and Innovation Newsletter May 21th 2025

Hello my fellow security enthusiast! Welcome back to a new another edition of the 'Security and Innovation' Newsletter. Get ready to continue diving into the world of Security and AI. Please share it with colleagues and friends to help our community grow. Happy reading! if you want a freebie, check the bottom of this newsletter :)
Open Source Strikes Back: New OSS companies challenges the GRC Giants
This is a very interesting development in the GRC world. While Vanta and Drata own the compliance automation space with their proprietary platforms charging thousands monthly, two open-source challengers are mounting a coordinated assault on the incumbents' business model.
The Disruptors:
Comp AI ($400K pre-seed) transforms compliance "from a vendor checkbox into an engineering problem solved through code," offering SOC 2, ISO 27001, and GDPR automation with full transparency and no vendor lock-in Comp AIGitHub.
Probo promises "SOC-2 ready in just 20 hours" with AI-powered policy generation and goes beyond software—they actually manage your entire audit process, finding auditors and handling compliance as a service Probo GitHub.
Both platforms offer what the giants don't: complete data ownership, export capabilities, and the ability to customize every aspect of your compliance stack GitHub - getprobo/probo: Open source solutions for SOC2, GDPR, and ISO27001. Probo even eliminates the traditional software friction by positioning itself as "your dedicated compliance team" rather than just another tool Probo.
The Disruption Potential: For cash-strapped startups tired of $10K+ annual contracts (in the best scenario) and enterprises demanding code transparency, this open-source duo offers compelling alternatives. With Comp AI targeting 100,000 companies by 2032 Comp AI - Crunchbase Company Profile & Funding and community-driven development accelerating features, the incumbents may soon face their biggest existential threat yet.
Bottom line: When two open-source projects attack the same market from different angles—pure platform vs. managed service—it signals serious trouble for proprietary compliance incumbents.
Having recently spoken with Lewis Carhart, Comp AI's founder, their execution velocity and technical progress are genuinely impressive. The team's developer-first approach isn't just marketing—they're shipping features at a pace that would make traditional vendors nervous.
How I ended up looking at this?
I'm currently helping a couple of startups to navigate ISO 27001, SOC 2, and ISO 42001 compliance in very aggressive timelines. The GRC solutions were simultaneously the most expensive part of their stack and the most useful, one having it the other not, the effort and efficiency difference is too much. That tension led me to dig deeper into alternatives—which is how I found these two new open-source players."
The Dawn of Coding Agents
This week was great for AI-powered development tools with three major announcements reshaping how we think about coding assistance. OpenAI unveiled Codex, Google introduced Jules, and Sourcegraph teased their upcoming AMP platform. While each tool shares the common goal of automating and enhancing the coding experience, they take distinctly different approaches to solving developer challenges. This convergence of releases signals we're entering a new era where AI agents don't just suggest code—they actively participate as coding partners, transforming software development from a purely human endeavor into a collaborative process between developers and intelligent systems. Opening new challenges to security teams.
So far I had the opportunity to play with AMP, and I liked their approach, waiting to get access to Jules next to test it. Codex Jules AMP
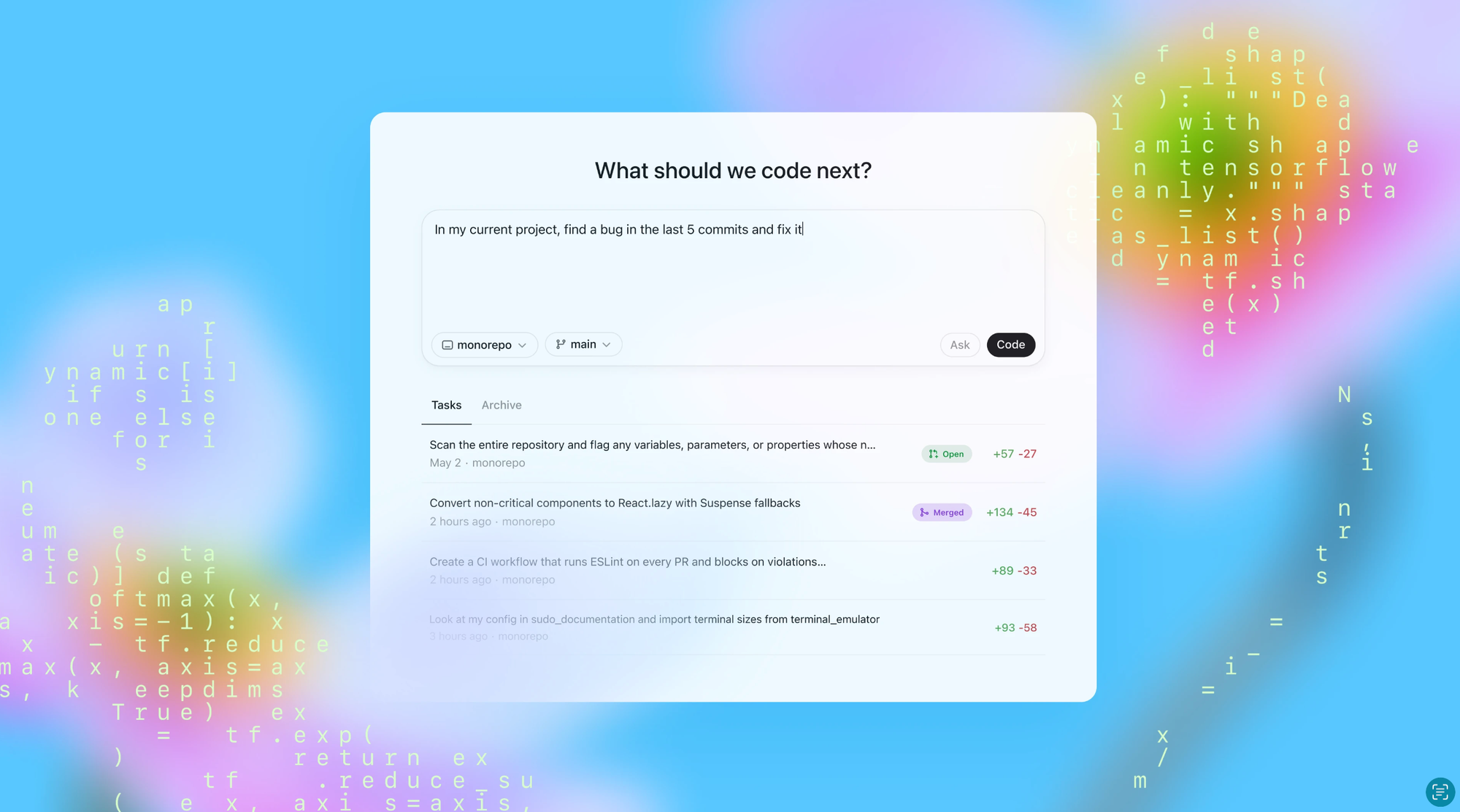
To follow up, the challenges of AI-generated code when it comes to risk:
Untested AI-generated code is a growing risk as many companies prioritize speed over quality, with two-thirds of teams pushing code without full testing. Despite high trust in AI for coding, most IT leaders anticipate major outages within the year due to unresolved security vulnerabilities. To mitigate these risks, companies must implement better governance and testing practices while clearly defining quality standards. Article
splx-ai/agentic-radar: A security scanner for your LLM agentic workflows
The Agentic Radar is an open-source security scanner designed to analyze and assess agentic systems for potential vulnerabilities and operational insights. Developed by splx.ai, it helps developers, researchers, and security professionals understand how agentic systems function and identify weaknesses. Key features include workflow visualization, tool identification, MCP server detection, and vulnerability mapping, all summarized in a comprehensive HTML report.
The scanner supports various frameworks such as OpenAI Agents, CrewAI, n8n, and LangGraph, with different levels of feature support across these platforms. It offers advanced funct ionalities like agentic prompt hardening, which improves system prompts following best practices, and runtime testing for vulnerabilities through simulated adversarial inputs. The project is licensed under Apache-2.0 and is actively maintained with regular updates and releases. Repo
Starting a Security Program from Scratch (or re-starting)
Great article from Phil Venables on creating Security program. Starting or re-starting a security program involves several phases, each with specific steps tailored to the organization's size and maturity level. The first phase focuses on getting the right direction by appointing someone from executive leadership to drive the initiative, establishing governance processes for decision-making and accountability, conducting critical systems security tests, and addressing high-risk results immediately.
The second phase emphasizes covering the basics through a broad security review using frameworks like the NIST Cyber Security Framework and CIS Critical Controls. This involves assessing and implementing essential controls such as secure configurations, privilege management, content filtering, endpoint defense, perimeter hardening, strong authentication, data isolation, regular backups, access management, and vendor checks.The subsequent phases involve making these basics more routine and sustainable, and eventually advancing to a strategic level of security maturity. The key takeaway is that while the specific steps may vary based on the orga nization's context, the framework provides a structured approach to building or rebuilding an effective security program. Article
GATO - GitHub Actions Pipeline Enumeration and Attack Tool
The "Gato" tool, developed by Praetorian Security Inc., is an advanced GitHub Actions Pipeline Enumeration and Attack Tool designed to help both blue teamers (defensive security practitioners) and red teamers (offensive security practitioners) identify and exploit vulnerabilities within a GitHub organization's public and private repositories. Gato offers features such as post-exploitation capabilities, which leverage compromised personal access tokens, and enumeration functions that pinpoint poisoned pipeline execution vulnerabilities and action artifacts secrets in public repositories. One of the key features introduced in version 1.7 is the Actions Artifacts Secrets Scanner. This tool downloads GitHub Actions workflow artifacts from target repositories, extracts them recursively, scans for secrets using NoseyParker, and reports the results. The scanner includes limitations to optimize scanning time, such as downloading a maximum of 50 artifacts per repository and avoiding files larger than 2.68 GBs. Repo
Food for thought
"Your words are simply reputation management" - Mark Manson
"I have three mentors.
When I’m stuck on a problem and need their help, I take the time to write a good description of my dilemma, before reaching out to them. I summarize the context, the problem, my options, and my thoughts on each. I make it as succinct as possible so as not to waste their time.
Before sending it, I try to predict what they’ll say. Then I go back and update what I wrote to address these obvious points in advance.
Finally, I try again to predict what they’ll say to this, based on what they’ve said in the past and what I know of their philosophy. Then, after this whole process, I realize I don’t need to bother them because the answer is now clear… None of them know they are my mentors.” - Derek Sivers
Member Spotlight: Security Strategy Blueprint
Most security leaders struggle with strategic direction. This week, I published my complete Security Strategy Canvas - the framework I developed over 25+ years building security programs at tech giants.
This isn't just theory. It's the same process I use with startups and enterprises to: → Map security landscapes → Identify business-critical gaps → Align security with business objectives → Communicate strategy to executives.
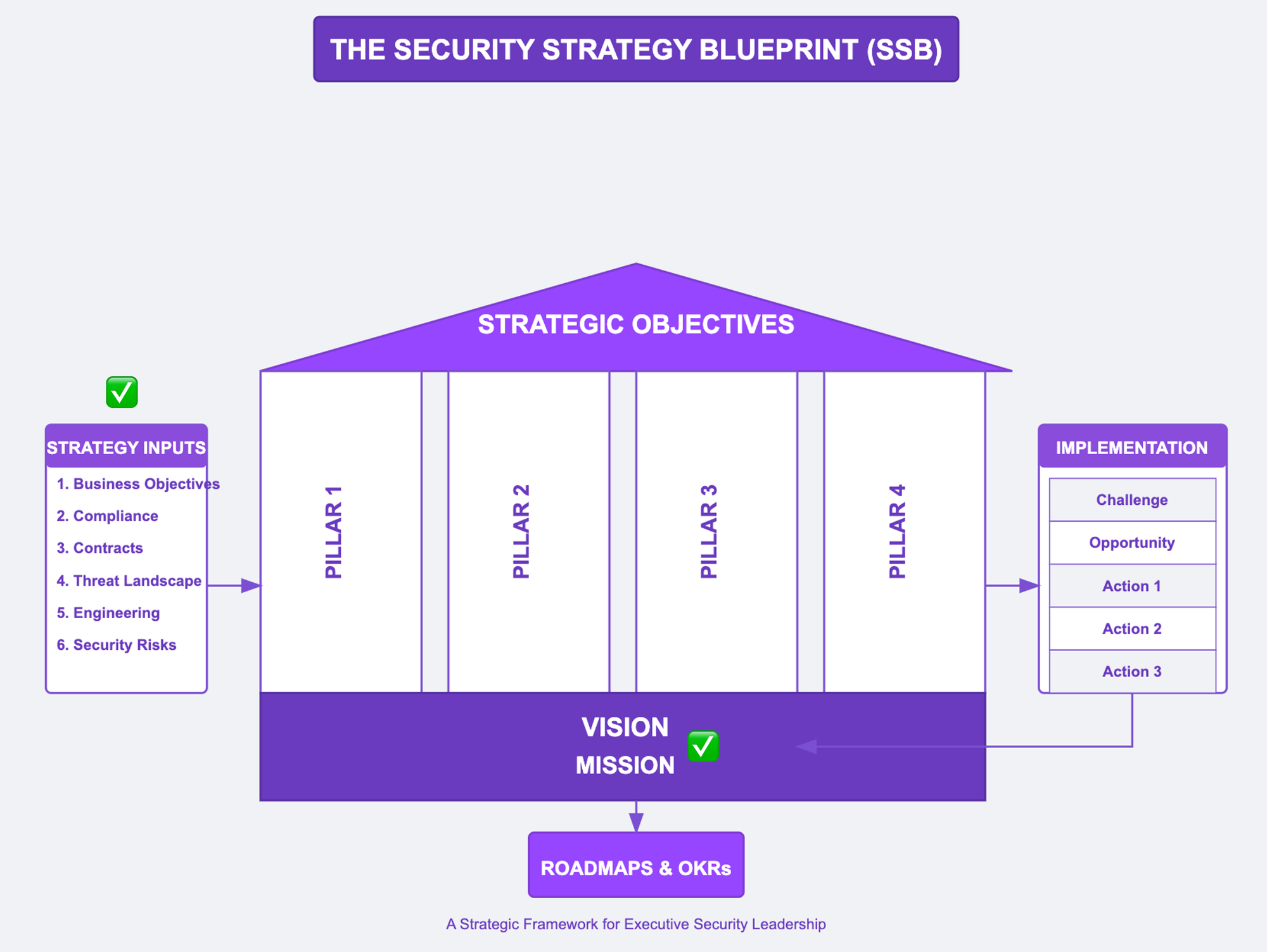
Originally presented at Barcelona Cybersecurity Congress, now available exclusively to members.
Get your Security Strategy Blueprint → HERE
Coming soon: Interactive Miro template version for team collaboration, as strategies are not a single person job :)
Enjoy
Chris Martorella
