The critical competencies that drive security career success -Part I
Welcome to this new article, today I want to share some tips about career development and what are considered the most important Skills for a Security professional. Hopefully this will be useful for you to develop and grow in your professional career .
Cybersecurity is an industry dominated by technical certifications, coding skills, and security frameworks, it's easy to overlook the critical role that soft skills play in cybersecurity success. While technical expertise is undoubtedly essential, the most effective security professionals aren't just technical experts—they're skilled communicators, strategic thinkers, and business partners.
Imagine this (or better said… "remember a time when), your team discover a critical security vulnerability through a technical means, but addressing it successfully requires influencing development teams to prioritize fixes, communicating risks effectively to management, understanding business impact across different departments, and making balanced decisions about implementation timing. Without strong soft skills, even the most technically brilliant security solutions may fail to get implemented or gain organizational buy-in.
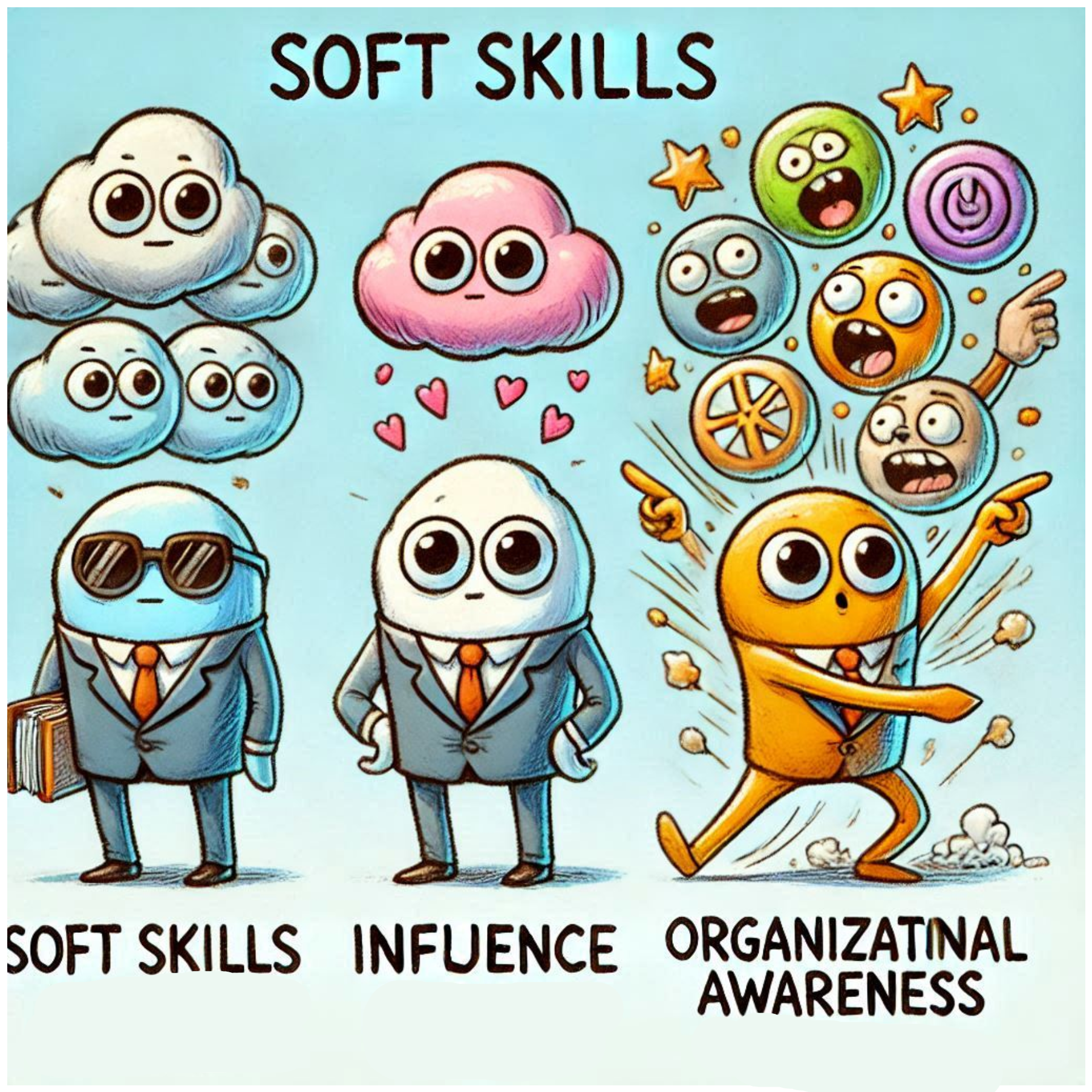
Many years back, I came across an article from CEB Inc, which doesnt exist anymore (was acquired by Gartner), that described the competencies of a High performance professional in Security. The article identified the fllowing 12 competencies:
| Competency | Definitions |
|---|---|
| ⭐ Business results orientation | Seeks to understand the business needs and deliver prompt, efficient, quality service to the business. |
| ⭐ Decision Making | Considers the relative costs and benefits of potential actions to choose the most appropriate one. |
| ⭐ Influence | Applies different strategies to convince others to change their opinions or plans. |
| ⭐ Organizational Awareness | Understands the organization’s mission, values, operations, and goals. |
| Communication | Conveys complex and technical issues to diverse audiences |
| Prioritization | Self-directs activities and works through goal setting, time management, and planning |
| Process Orientation | Uses practices, processes, procedures, and systems to manage work and to simplify and use resources efficiently |
| Learning Agility | Rapidly acquires new knowledge and learns new skills |
| Relationship Management | Creates relationships with new acquaintances quickly and confidently |
| Teamwork | Promotes and facilitates coordination and cooperation among peers |
| Analytic Ability | Effectively uses science, statistics, and computer technology to solve problems |
The study stated that all 12 competencies are important but the first 4 have a disproportionate greater impact on performance. This is great, so we can follow the rule of the 80/20 and focus on the skills that will bring the biggest return on investment. These have much better impact and are far more relevant than years of experience, educational background (degree, professional certifications).
Industry surveys and job market analyses consistently show that employers value soft skills alongside technical capabilities when hiring security professionals. This is reflected in job postings that increasingly emphasize communication skills, business acumen, and leadership potential alongside technical requirements.
What is a competency?
Competency: A set of knowledge, skills, and abilities required to deliver a desired objective
- Knowledge: An individual’s familiarity with information, facts, or descriptions acquired through experience or education
- Skill: An individual’s proficiency at performing a learned activity
- Ability: An individual’s innate proficiency at and potential to perform a specific behavior at a higher proficiency
These are measured via behaviours, and that´s how you will see them used in development plans and included as part of Career development and performance reviews.
Developing these skills
I hear you! How can I develop these competencies? They are too abstract, I am dont know how they look like...
No worries, In this section I share a process and material to help security professional to develop the soft skills that are most impactful for their career. Here are two examples for Influence and Organizational Awareness. Every skill will have strategies or recommendations with examples and links when available.
Business Results Orientation
Is the ability to understand, prioritize, and align security initiatives with business objectives to deliver measurable value and outcomes. It involves developing solutions that balance security requirements with business efficiency, growth targets, and customer needs while maintaining a focus on quantifiable results and return on investment.
Here are some strategies that will help to develop this business result orientation:
| Strategies and recommendations | Link to resources and examples |
|---|---|
| Track and Measure Security Impact: Develop metrics and KPIs that demonstrate the business value of security initiatives, including cost savings, risk reduction, and operational efficiency improvements. | Security dashboards, incident response metrics, risk assessment reports, ROI calculations for security investments |
| Align with Business KPIs: Learn to translate security objectives into business terms and demonstrate how security initiatives support key business metrics like revenue growth, customer satisfaction, and market expansion. | Company OKRs, quarterly business reviews, departmental performance metrics. |
| Develop Cost-Benefit Analysis Skills: Practice creating business cases for security initiatives that clearly articulate the value proposition, required resources, and expected returns. | Project proposals, budget planning documents, resource allocation frameworks. Build vs buy |
| Focus on Customer Impact: Consider how security decisions affect customer experience, satisfaction, and trust. Balance security controls with user experience and business agility. | Customer feedback channels, NPS scores, user experience metrics. Listen to your internal customers :) |
| Prioritize Based on Business Risk: Develop a risk-based approach to security that considers both technical vulnerabilities and business impact when prioritizing security initiatives. | Risk assessment frameworks (NIST, FAIR), business impact analysis templates |
| Study Business Operations: Invest time in understanding core business processes, revenue streams, and operational workflows to identify where security can add the most value. | Process documentation, workflow diagrams, revenue models |
| Build Financial knowledge: Develop basic financial literacy to better understand budgets, cost structures, and how security investments impact the bottom line. | Financial reports, budget planning tools, ROI calculators |
| Streamline Security Processes: Continuously look for ways to optimize security operations and reduce friction in business processes while maintaining appropriate security controls. | "If you get one percent better each day for one year, you’ll end up thirty-seven times better by the time you’re done." |
| Monitor Industry Trends: Stay informed about industry developments that could impact both security and business objectives, helping to anticipate and prepare for future needs. | Industry reports, competitor analysis, market trends. |
| Develop Solution-Oriented Mindset: Focus on finding ways to enable business initiatives securely rather than simply identifying security blockers. | Security architecture reviews, alternative solution proposals. Instead of starting with "No", it's better to start with Yes, but.. there is always ways to find a working solution that balance security and business needs. |
| Measure and Communicate Success: Regularly report on security achievements in business terms, highlighting both quantitative and qualitative benefits to the organization. | Executive dashboards, success metrics, business impact reports. Quarterly Business reports, All hands. Blog article |
Thinking time
- How comfortable are you discussing security in terms of Return on Investment (ROI) and business value?
- How do your current security projects directly support business objectives?
- Can you explain your organization's revenue model and key business metrics?
- When was the last time you modified a security control based on business feedback?
This competency is crucial for Security Engineers because it ensures that security measures enhance rather than hinder business operations, helping to position security as a business enabler rather than just a cost center.
Decision Making
Is the ability to systematically evaluate security challenges, risks, and opportunities to make well-reasoned choices that balance security requirements with business needs. It involves gathering and analyzing relevant information, considering multiple perspectives, assessing trade-offs, and taking decisive action while being accountable for outcomes. This competency enables security professionals to navigate complex scenarios where perfect solutions may not exist (which is usually the case).

This competency is essential for Security professionals as they frequently face decisions that impact system security, user experience, resource allocation, and business operations. Here are strategies to develop strong decision-making capabilities:
| Strategies and recommendations | Link to resources and examples |
|---|---|
| Develop a Structured Analysis Framework: Adopt and consistently use decision-making frameworks that help evaluate problems from multiple angles, including technical, business, and risk perspectives. | 10 Decision Making frameworks NIST Risk Management Framework, FAIR (Factor Analysis of Information Risk) |
| Practice Data-Driven Decision Making: Base decisions on quantifiable metrics and evidence rather than assumptions. Gather relevant data and metrics to support your decision-making process. | Security metrics dashboards, incident data, vulnerability scanning results, compliance reports |
| Document Decision Rationale: Maintain clear records of significant decisions, including the context, alternatives considered, criteria used, and expected outcomes. This creates a valuable reference for future decisions. | Decision logs, architectural decision records (ADRs), project documentation. |
| Build Stakeholder Analysis Skills: Identify and understand the perspectives of all stakeholders affected by security decisions, including technical teams, business units, and end users. | Stakeholder mapping tools, impact assessment templates, Design reviews. And mainly be mindful on how the decision will impact other stakeholders. |
| Study Past Incidents and Decisions: Review historical security incidents and decisions to understand what worked, what didn't, and why. Use these insights to improve future decision-making. | Post-incident reports,Post mortems, lessons learned documents, case studies |
| Develop Risk Assessment Expertise: Strengthen your ability to evaluate and compare different types of risks, including their likelihood, potential impact, and mitigation costs. | Get famililar with your company Risk assessment framework, If there isnt any in place yet, find and standard one and get familiar using it, same for Threat modeling methodologies. |
| Practice Time-Critical Decision Making: Develop protocols and guidelines for making rapid decisions during security incidents while maintaining quality and accountability. | Incident response playbooks, decision trees, escalation procedures. |
| Seek Multiple Perspectives: Actively consult with colleagues and subject matter experts to gather diverse viewpoints before making significant decisions. | Security working groups, peer reviews, expert consultations. Dont be shy to ask for help, reviews or other points of view! |
| Understand Decision Impact: Evaluate the downstream effects of security decisions on systems, processes, and people across the organization. | Impact analysis templates, dependency mapping tools. Again be mindful on how the decision will impact other stakeholders. |
| Build Change Management Skills: Learn to effectively implement and communicate decisions, including managing resistance and ensuring smooth transitions. | Change management frameworks, communication templates. This is key to ensure your hard work is properly roll out into the organization. If you have a great process but nobody is aware of it, it is the same as not having it. |
| Develop Contingency Planning: Create backup plans and exit strategies for major decisions to manage potential negative outcomes. | Contingency planning templates, rollback procedures. Jeff Bezos, How successful people make such smart decision.(easy vs difficult to reverse decisions) |
Thinking time
- What framework do you currently use to make security decisions?
- How do you balance different types of risks when making security decisions?
- Can you recall a recent decision where you had to choose between competing priorities?
Remember that good decision-making in security often requires balancing competing priorities:
- Security vs. Usability
- Speed vs. Thoroughness
- Cost vs. Risk Reduction
- Innovation vs. Stability
- Immediate vs. Long-term Benefits
The key is to remain flexible and adapt your decision-making approach based on the situation's urgency, impact, and complexity.
These first two core competencies - Business Results Orientation, Decision Making- form the foundation of high-performing security professionals. While technical skills remain important, developing these soft skills creates disproportionate impact on career growth and effectiveness.
Remember that growth in these areas is iterative - focus on continuous improvement rather than perfection
Next article will focus on Organizational awareness and Influence, to complete this set of most critical competencies you can develop.
