The Security Strategy Blueprint: From Vision to Implementation

How to build a security strategy step by step.
This article provides a practical framework for security leaders to create and implement effective security strategies that align with organizational goals while addressing complex threat landscapes.
A well-designed cybersecurity strategy serves as more than just a security roadmap—it provides clear direction, improves employee engagement, enhances decision-making, and ensures better resource allocation across the organization. The strategy development process requires careful consideration of multiple factors, including business objectives, compliance requirements, contractual obligations, threat landscape analysis, and existing security risks.
It is one of the main responsabilities of a Security leader to build an effective Security a strategy, in order to provide direction, clarity, alignment and prioritization. But not everyone has experience doing this, and not everyone is aligned on what is a Strategy or how it should look like. I remember struggling at the beginning when trying to understand the differences of Strategy, plan, tactics, objectives, goals, etc. aren't all the same?
Let's start with the basics and understand what do we mean by Strategy.

What is a strategy?
Initially, the concept of strategy was primarily associated with military planning and warfare. The word “strategy” has its origins in ancient Greek military terminology. It derives from the Greek word “stratēgía” (στρατηγία), which meant “office or command of a general”. The term is composed of two parts: “stratos” (army) and “agein” (to lead).
Why do we want a strategy?
Having an strategy in place, will provide some benefits like:
Organizational benefits:
- Clearer direction and focus: A clear security strategy aligns all teams toward common objectives, transforming security from a reactive function into a strategic enabler. Teams understand not just what they're doing, but why their work matters to the organization's success.
- Enhanced communication and collaboration The strategy creates a shared language and framework across teams and organizations, breaking down silos between security, engineering, and business teams. This improved communication ensures everyone understands their role in achieving security objectives.
Operational benefits:
- Improve decision making: The strategy serves as a decision-making framework, enabling teams to evaluate options and make choices that support long-term security goals while addressing immediate needs
- Resource optimization: With clear strategic priorities, organizations can make informed decisions about resource allocation, ensuring investments in security tools, technology, and talent align with business needs.
- Better accountability: By establishing clear responsibilities and success metrics and outcomes, the strategy creates a culture of ownership where teams understand their deliverables and impact.
Cultural benefits:
- Employee Engagement and Purpose: In my experience leading security teams, this is one of the most transformative benefits. When teams transition from reactive firefighting to strategic, proactive security work, their sense of purpose and job satisfaction significantly increases.
- Security-First Mindset: A well-communicated strategy helps embed security thinking into the organizational culture, making it everyone's responsibility rather than just the security team's concern.
As you can see, those benefits are all related with each other. The results are very positive and definitely what every leader desires for his/her teams.
From Strategy to Implementation: A Practical Approach
Now that we understand why a security strategy is crucial, let's explore when and how to develop one effectively. The timing and approach of strategy development are as important as the strategy itself.
Do I need one now ? When is the right time to create one?
There are different opinions on when to have an Strategy in place, I believe in part is due to the different understanding when people hear the word Strategy, some people think on long term 2-3 years document, outlining all the domains in depth, entailing pages and pages of documentation, that very few people end up reading. But also it can be something short that provides some clarity on the direction and priorities as organization that needs to be tackle.
Before diving in and rush into creating your strategy as soon as you join a new organization, first consider your organization's current state, its trajectory, and whether you have enough knowledge to be effective at this point. That means that you need to understand the business strategy, wider organization like Engineering and Product strategy state and priorities, how the security teams were working until now and once you have a understanding of all this you will be in a position to start putting together your strategy.
When I joined Skyscanner, there was no Security strategy in place, but there was mature Engineering organisation with heavy focus on Standardisation (this is amazing for Security), in that case I had to build the practice from almost scratch. I did an assessment based on the maturity model, but used that to understand where we were in the Security journey and where we will have to invest in the short term and how to structure the teams to achieve the basics. But in order to build the first Strategy, I had to consider much more than a Maturity posture analysis of the Cybersecurity domain, I needed inputs from multiple domains, areas and levels that takes time as a new leader to understand.
Components of an Effective Security Strategy
Building on our understanding of when to create a strategy, let's examine the essential components that make a security strategy comprehensive and actionable. Each component serves a specific purpose in creating a robust security posture.
The process of creating a cybersecurity strategy is both complex and multifaceted, requiring a deep understanding of various interconnected elements. At its core, a well-designed cybersecurity strategy serves as a roadmap for protecting an organization’s digital assets, aligning security measures with business objectives, and ensuring compliance with regulatory requirements. It’s not just about implementing the latest security technologies; or addressing the latest attack, it’s about developing a holistic approach that addresses the unique needs and challenges of the organization.
There are many components involved, and here we cover the key inputs needed to create a succesful strategy:
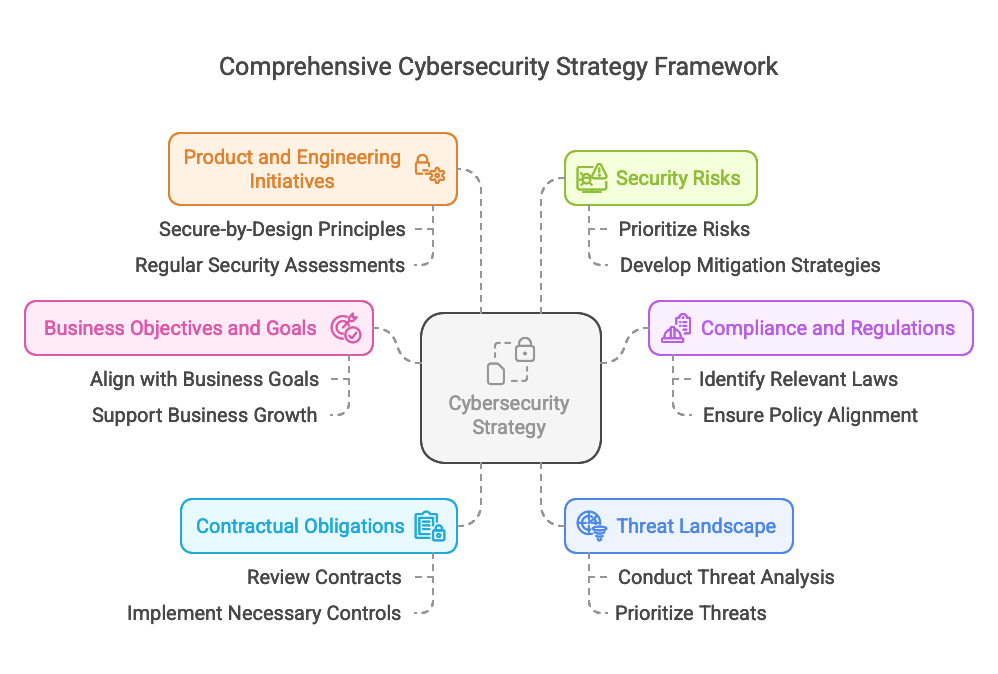
Business objectives and goals: Aligning security objectives with business goals is crucial for an effective security strategy, after all that's why are here. This involves:
- Understanding the organization’s mission, strategic direction, and long-term objectives
- Identifying how security initiatives can support and enable business growth.
- Expanding to new markets? Integrations? Partnerships? Acquisitions?
Compliance and regulations obligations: A comprehensive security strategy must address relevant legal and regulatory requirements:
- Identify applicable laws, regulations, and industry standards (e.g., GDPR, HIPAA, PCI DSS, DORA, NIS)
- Ensure security controls and policies align with compliance requirements
Contractual obligations: Security strategies should account for contractual commitments to clients, partners, and vendors:
- Understand existing contracts to identify security-related clauses and requirements (Partner up with Legal)
- Include necessary controls to meet contractual security obligations as part of the strategy.
- Understand what your key customers require to ensure that your company well equiped to breeze throug the deals.
Threat Landscape: Understanding the current and evolving threat landscape is essential for a robust security strategy, what are the the most relevant threats and actors for your business and technology profile:
- Assess the organization’s specific threat profile based on industry, size, and geographic location
- Prioritize threats based on their potential impact and likelihood of occurrence
- Develop strategies to address both current and anticipated future threats
- You can use Threat Intelligence reports like Verizon DBIR and similars to feed in this part. I recommend having 2 or 3 to ensure you are not biased by the approach taken by the companies producing those reports.
Product and Engineering initiatives: Understanding what are the priorities for the Product and the engineering organization, what initiatives are already in flight and which ones you will have to support, which ones you can slipstream on:
- Establish security requirements and controls for new products and features
- Some examples are migrations, cloud adoption, multi cloud strategy, reorganisations, new regions, new technologies,
Security Risks: Last but not least, Identifying and managing security risks is a core component of any security strategy:
- Prioritize risks based on their severity and potential business impact
- Develop risk mitigation strategies and implement appropriate security controls
- Establish a continuous risk management process to address evolving threats and vulnerabilities
These are all inputs and considerations that you need to work with when you start creating a Cybersecurity strategy. This will create a holistic picture about your business posture and needs.
Every section is important and will contribute to have a solid and comprehensive strategy, and that's why creating a cybersecurity strategy is inherently more challenging than developing strategies in many other domains due to the multifaceted nature of the digital threat landscape and the numerous considerations that must be taken into account. The rapidly evolving technological environment, coupled with the increasing sophistication of cyber threats, requires a strategy that is both comprehensive and adaptable, letting you change course and adjust when needed.
Bringing It All Together
With these components in mind, we can now explore a practical framework for organizing and documenting your security strategy. The Strategy House framework provides a clear structure that connects high-level vision to tactical execution. I like this classic approach from consulting firms like McKinsey, Bain and BCG that provides a clear structure to document an Strategy. This format tipically has:
Foundation:
- Vision: A forward-looking declaration of what an organization hopes to achieve in the future. It acts as a “North Star” by inspiring employees and stakeholders while guiding long-term planning.(This is your Security Vision, not the company)
- Mission: Defines the organization’s (in this case Security) purpose, explaining why it exists and how it adds value to its community or customers. It provides a foundation for strategic goals and day-to-day operations.
Pillars: Key focus areas or initiatives. In order to structure the work, we can separate it in Pillars, that basically will focus in a particular domain or theme.
Roof: Overarching goals or objectives. Inside the Initiatives we will have goals and objectives that we want to achieve with our strategy. (these will be turned in projects, OKRs, etc)
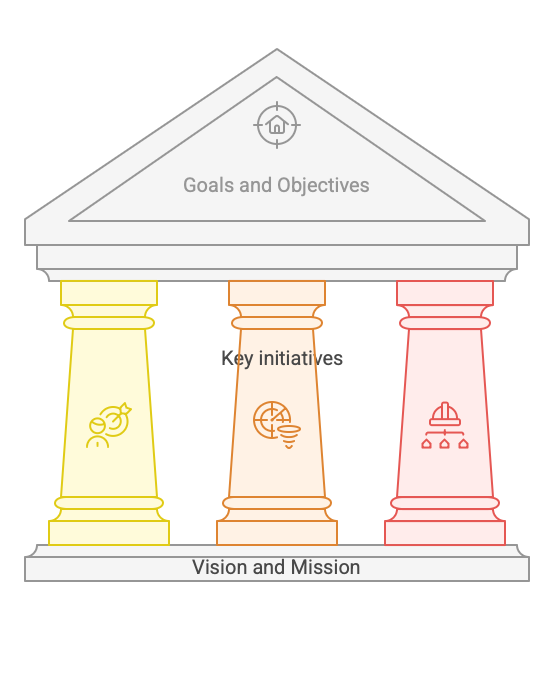
Don't start your house by the roof!
Challenge-Opportunity Approach:
Now to get into the details I like to use the approach "Challenge-Opportunity", as outlined in Richard Rumelt’s “Good Strategy/Bad Strategy,” . This approach focuses on identifying and addressing critical challenges while leveraging opportunities to create a coherent and actionable strategy.
The Kernel of Good Strategy
At the core of Rumelt’s approach is the concept of the “kernel” of good strategy, which consists of three elements:
1. Diagnosis: Identifying the critical challenge or opportunity (We have all the input from the previous phase)
2. Guiding Policy: Developing an overall approach to overcome the challenge
3. Coherent Actions: Implementing specific, coordinated steps to execute the guiding policy
I like to use a table approach for this part, usually one table per Strategy pillar to make it easier to manage. Here is an example of how it looks like for Secure by design pillar.

Work with Challenges: Focus on barriers and issues rather than performance goals or end-states.
Prioritize and Focus: Narrow down the list of challenges of critical issues that can be addressed in the near future, with the resources available (6-12 months)
Design Coordinated Actions: Develop a set of coherent actions that work together to address the identified challenge or opportunity.
Finally create roadmaps (one per team, domain, or pillar) out of those identified challenges, and opportunities and Actions, and operationalize with your framework of choice in my case in the last few years we used OKRs and GOST models. (not going to go in details in this article)
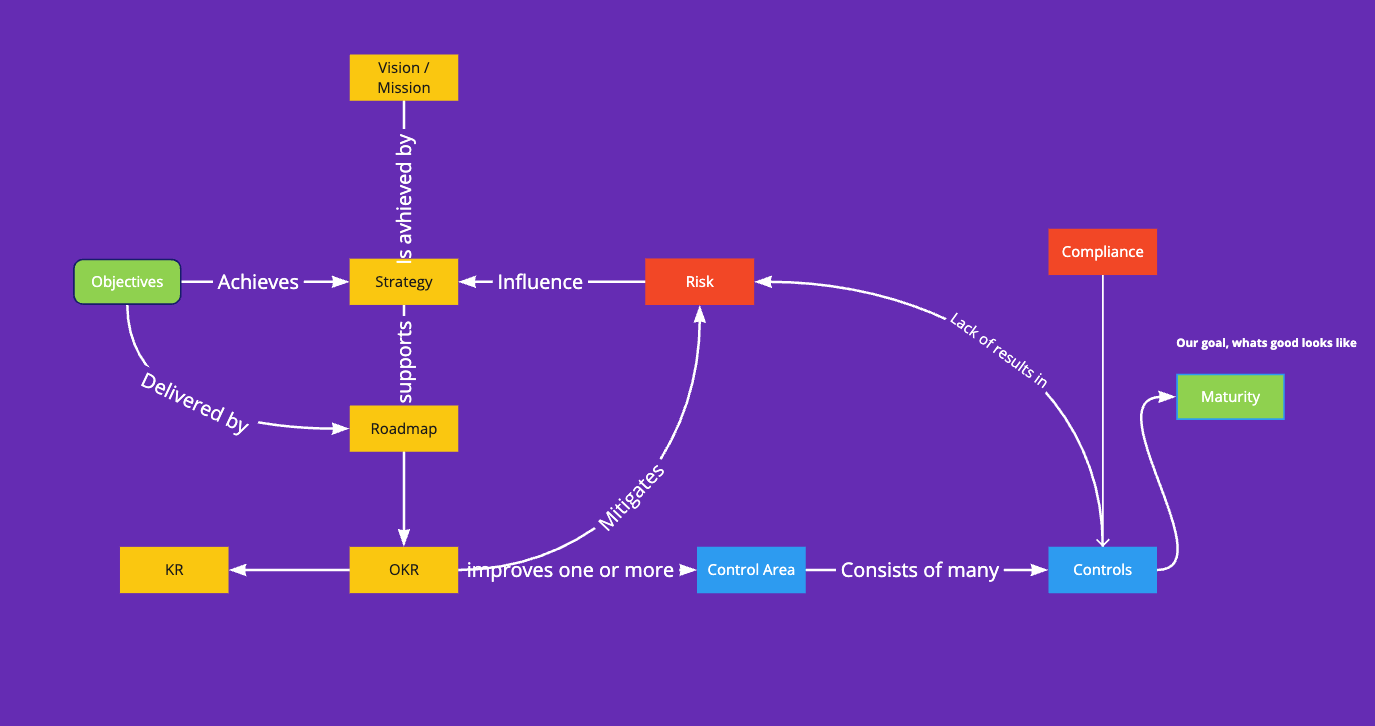
So if you look at all the pieces together, you can get a process that maps, Vision, Mission, Strategy, Objectives, Roadmaps, OKRs, Risks, Controls and finally Maturity, and this will enable to map Security initiatives to the business goals and objectives.
This a continous process, you revise and adjust and correct course as needed. Your strength will be in the adaptability and being able to enable the business to move faster in a secure way.
An picture worth thousand words (thanks to Veroniki Stamati, who came up into one image the whole process we had in Skyscanner)
Finally, it's important to understand if the company has a different approach to writing strategies, what other areas are doing. I remember that when I joined Miro, Engineering was working on the "Engineering Painted Picture":
A vivid description of what success looks like at a specific point in the future. This tool helps organizations visualize their goals in detail, creating a shared understanding of what they are working toward.This is kind of North Star, but on steroids. If that is the way organization communicates vision, objectives and goals, you probably want to adapt the output of your strategy to ensure you can align with the rest.
There are more things that could be discussed and considered in this article, but I think this covers the essence of building a comprehensive Cybersecurity Strategy.
Things to avoid...
During the last few years I learnt a lot about creating, modifying and discarding strategies, and made some miss-takes on the way. Here are some of the most important bits I want to share with you so you can avoid them early on.
- Starting an strategy solely on the maturity assessment and focusing on increasing maturity only of your capabilities, without focusing on the threat landscape, risks and business objectives, as this will place the efforts in the wrong initiatives, wasting resources.
- Implement an Strategy too soon: numerous new leaders, in their eagerness to demonstrate immediate value, often rush to implement broad changes without first gaining a thorough understanding of their new organizational context. I saw examples of people jumping in to conclusions and push for certain initiatives without yet understanding the company culture and current situation and how and why things work. Obviously only to realise about this when it was late and wasted enormous resources and social capital.
- "Avoiding the traps of writing so much that it’s ignored or so little that there’s not much impact" As put by Lethaim in his article about Engineering Strategy.
- Making too complex and difficult to understand, avoid jargon and Acronyms as much as possible. Make it simple and easier to understand for all stakeholders.
I hope you enjoyed this article, and you find it useful to write your first Strategy or improve your existent one.
If you need help with your strategy work, feel free to reach me.
Chris
